While looking for issues in your application, you may employ different practices, such as penetration tests, vulnerability scanning, risk assessments, etc.
Although these methods can give valuable results, there is a way to use the skills of highly talented professionals outside your organization to find bugs through their unique, fresh perspectives.
In this article, we will talk about the bug bounty program—a well-established practice that can help you uncover some difficult-to-find bugs and security flaws in your application.
By the end of the article you will have a better understanding of bug bounty programs and the benefits they can offer.
Table of Contents
What is a bug bounty program
A bug bounty or vulnerability rewards program is a practice where you reward individuals for finding bugs in your product and reporting them back to you.
This kind of program is a way to supplement penetration testing procedures and code reviews within your organization by using the skills of talented professionals outside of it.
These crowdsourcing initiatives allow ethical hackers and security researchers to detect cybersecurity bugs, authorizing them to access and test your application and report any issues in exchange for a prize or payment.
You can design bug bounty programs in various ways—from public programs where anyone can sign up to private, invite-only programs if confidentiality is a concern.
The scope of the testing can also vary:

While some companies can decide to allow ethical hackers to test the entirety of their application for vulnerabilities, declaring an open season on bugs, others can specify which issues can be tested and are eligible for rewards and which aren’t.
Companies will generally discourage things like large-scale denial-of-service attacks as they can put unnecessary strain on the application and instead encourage finding some common security vulnerabilities like cross-site scripting issues.
After these hackers discover bugs, they make a comprehensive bug report, usually through third-party programs like HackerOne or a dedicated bug reporting platform owned by the company.

Get unreal data to fix real issues in your app & web.
If the bug is deemed valid, the organization may work with the ethical hacker to validate it, patch it, and verify if it’s fixed.
If the bug report was helpful, the company organizing the bug bounty then pays the individual responsible for reporting the bug.
The sum varies depending on the severity and impact of the bug.
Bug bounties aren’t a new practice by any means, having existed for over two decades:
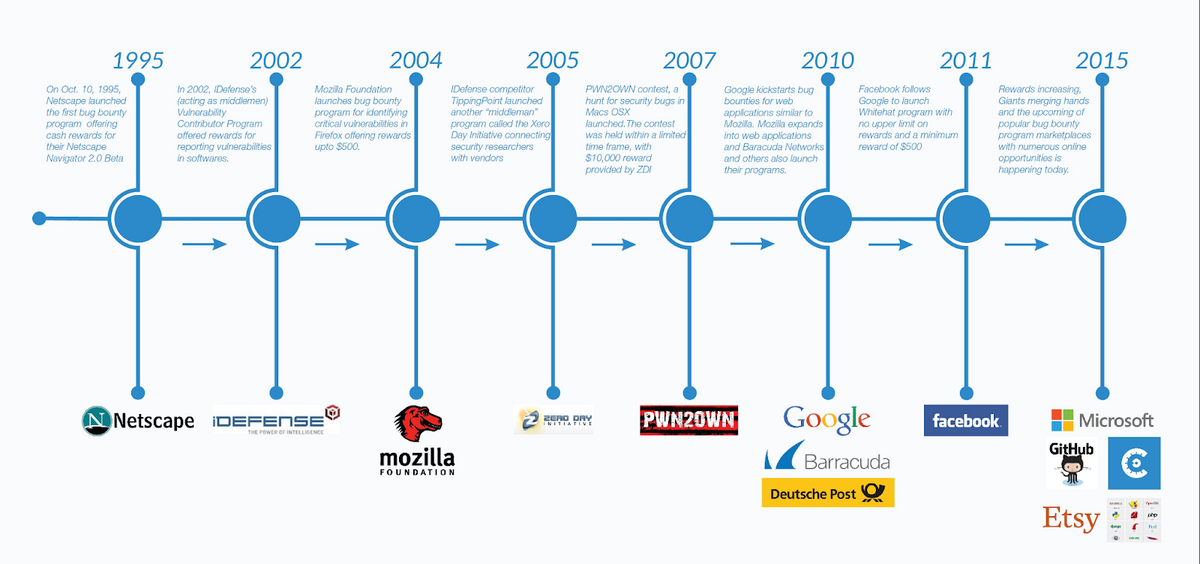
Netscape created the first bug bounty program in 1995, offering compensation for individuals that could find security defects in their Netscape Navigator 2.0 Beta.
Matt Horner, Netscape’s vice president od marketing at the time, explained their program like this:
By rewarding users for quickly identifying and reporting bugs back to us, this program will encourage an extensive, open review of Netscape Navigator 2.0 and will help us to continue to create products of the highest quality.
Although other companies didn’t initially understand the value of Netscape’s bug bounty program, eventually more big players followed suit.
Some notable examples are the 2004 Mozilla Firefox Bug Bounty, which is still being implemented today, Google’s program that was established in 2010, and Facebook’s white hat program, which began in 2011.
Today, businesses of various sizes implement similar bug bounty programs, and the bounties have steadily increased as these programs have grown in scope and popularity.
Why do companies launch bug bounty programs
Bug bounty programs are usually conducted by businesses who are confident in the effectiveness of their vulnerability testing procedures and want expert verification that they haven’t missed anything.
You can view these programs as an additional way to ensure there aren’t any hidden, severe defects in your software by using outside professional help.
There are several advantages to this practice.
Detecting severe bugs
However rigorous your testing procedures may be, your team can sometimes miss a glaring flaw in your application.
These mistakes don’t have to be an issue if the flaw isn’t significant in scope, but they can be highly problematic if they miss a high-severity security bug.
By giving financial incentives to hackers and testers, your organization can attract many highly skilled individuals and increase the chances of finding these bugs and exploits before they hurt your business.
If a cybercriminal discovers and exploits severe vulnerabilities before you can fix them, the impact on your organization could be far-reaching:

Ethical hackers can find severe bugs before malicious individuals do, which will allow you to handle these issues and avoid the costs of a security breach and potentially having to pay damages to your users.
With a bug bounty program, an organization has a higher chance of identifying vulnerabilities before they can be used in attacks.
This helps protect the company’s reputation and decreases the likelihood of high-value hacks.
Simulating real threats
Although your company can run in-house or outsourced penetration tests and vulnerability assessments, these procedures may have drawbacks.
The conducted tests may not be comprehensive enough to find all serious threats, the results can be misleading and give a false sense of security, and tests can fail due to being limited by time and resources.
To remedy this issue, you can use bug bounty programs and benefit from the talents of white hat hackers:
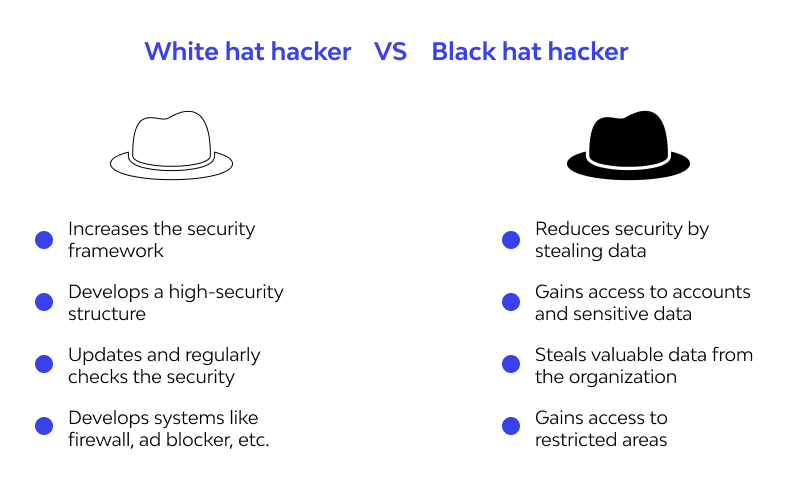
By using bug bounty programs, white hat hackers can help your company find and report bugs by thinking similarly to the way a malicious hacker may think.
These malicious or so-called black hat hackers are skilled criminals who use vulnerabilities in your software with malintent, exploiting them for their own benefit.
Ethical hackers and security researchers can have a similar skillset to these individuals, a larger timeframe for finding bugs and a high level of motivation to find critical flaws in your app, due to the prizes you offer.
By launching bounty programs, you may simulate an attack from individual hackers or hacker groups by paying people to act like cybercriminals and see if your software can withstand their attacks.
This procedure can provide more realistic and valuable insights than the structured and highly specific penetration tests that are usually conducted and give you a more accurate picture of the vulnerabilities of your software.
Saving costs
Compensating ethical hackers for finding security bugs will be cheaper than dealing with a real-life breach, so cost-effectiveness is another great benefit of bug bounty programs.
Just look at the statistics from a 2022 IBM report:
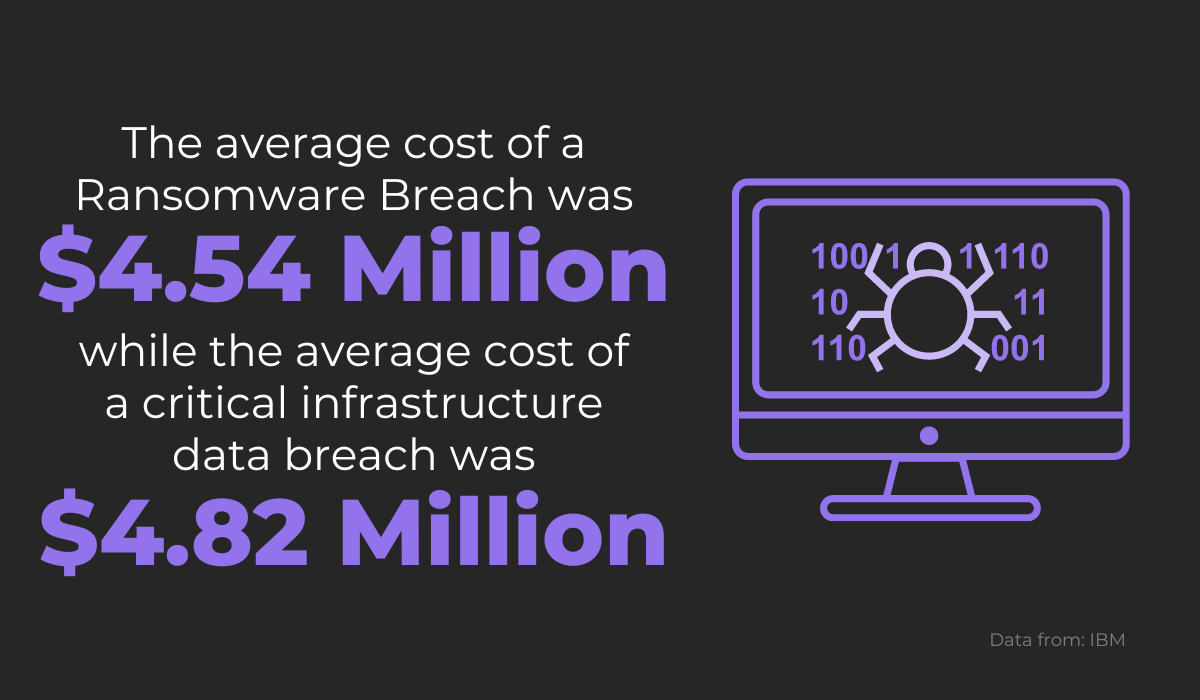
These security breaches are especially damaging if your company is in the healthcare, finance, or technology industries.
In fact, healthcare incurs the highest data breach costs, with an average of 10.1 million US dollars per breach.
This is a huge sum compared to the average rewards you might give bounty hunters for finding bugs.
According to a report by HackerOne in 2021, the median price for bugs is $3000 for critical bugs, $1000 for high-severity ones, $500 for medium, and $150 for low-severity bugs.
And if you are still hesitant about the costs, remember that ethical hackers are only compensated if they find something, instead of being paid by the hour.
In summary, bug bounty programs can be a cost-effective way to simulate real hacker attacks while simultaneously fixing any potential vulnerabilities that are found by highly skilled professionals before black hat hackers abuse them.
Should you launch a bug bounty program
After reading the previous sections, you may be thinking about starting your own bug bounty program.
When considering this practice, you should first weigh the advantages and disadvantages it can bring to your company.
Although a bug bounty program can give you great benefits, as discussed in the previous section, there are also certain drawbacks you should be aware of:
In the same way that internal test teams can miss some bugs and issues in your app, there is no certainty that outside collaborators will have similar blind spots.
Even though bug bounty programs increase the diversity of people included in testing your app for problems, bounty hunters still have a different perspective than professional testers, hackers, or end-users.
The motivation of these ethical hackers is different as well.
If your company plans on giving sizable bounties to participants, you may attract a lot of experts.
However, most of them will probably go after the biggest prizes, gained for finding critical or severe issues—ignoring low and medium-severity bugs which can pile up and cause problems later down the line.
Another issue is the potential lack of communication between your company and the participants.
Due to the nature of these programs, miscommunication can arise at any point.
For instance, maybe the hacker hasn’t explained the bug well enough in the report so your team can’t reproduce it and verify it.
Or, perhaps you haven’t written a good enough security policy, leaving participants confused about which vulnerabilities are okay to test and which aren’t.
Keeping these disadvantages in mind, a bug bounty could still be beneficial if you have already detected and fixed the main issues in your software and want to pinpoint the few harder-to-find bugs and exploits.
And the number of these hidden issues can be pretty significant:
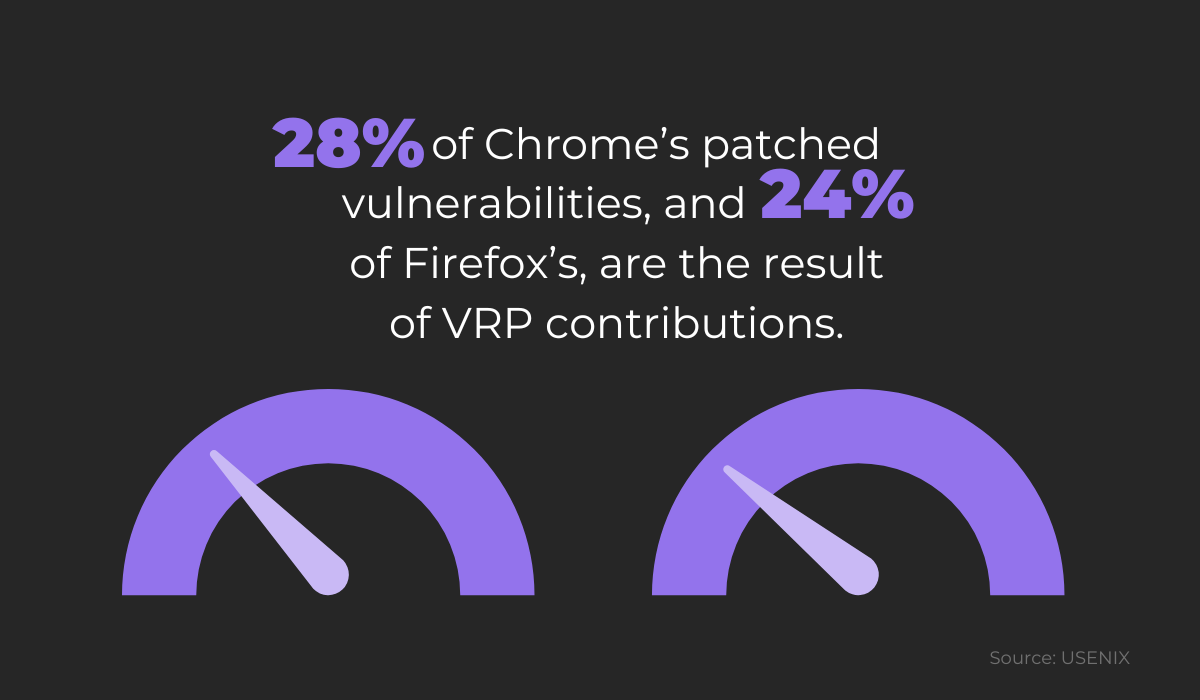
This study cited above was conducted in 2013, with the aim of determining the cost of the Chrome and Firefox Vulnerability Rewards Programs (VRP) over the course of three years.
It also showcased the benefits of these programs in identifying security vulnerabilities.
As you can see, roughly a quarter of the bugs found during this period were due to the contribution of outside collaborators.
This benefit can be considered highly valuable, especially when compared to the relative cost these companies had when paying participants.
So, evaluate the costs and benefits of bug bounty programs and decide for yourself if implementing one is a good idea for your organization.
Examples of bug bounty programs
If you have already decided to create a bug bounty program of your own, read on to get some inspiration on how to organize it by following the example of already existing programs.
As mentioned earlier, you can take pointers from some of the tech giants that organize bug bounty programs, such as:
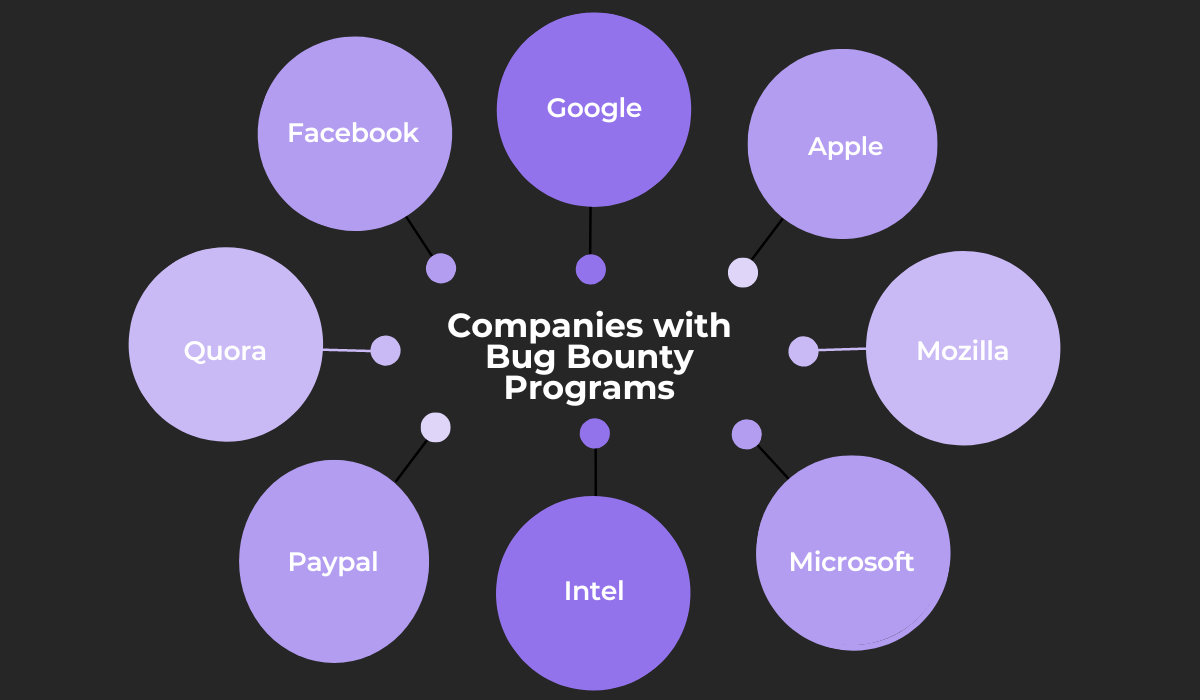
Let’s look at Google’s Vulnerability Reward Program (VRP) program as an example of a thoroughly planned bug bounty program, where every service owned by Google is open for testing.
Google’s VRP has strict rules covering the bugs eligible for a prize, the prize money, and the vulnerabilities they want participants to focus on:
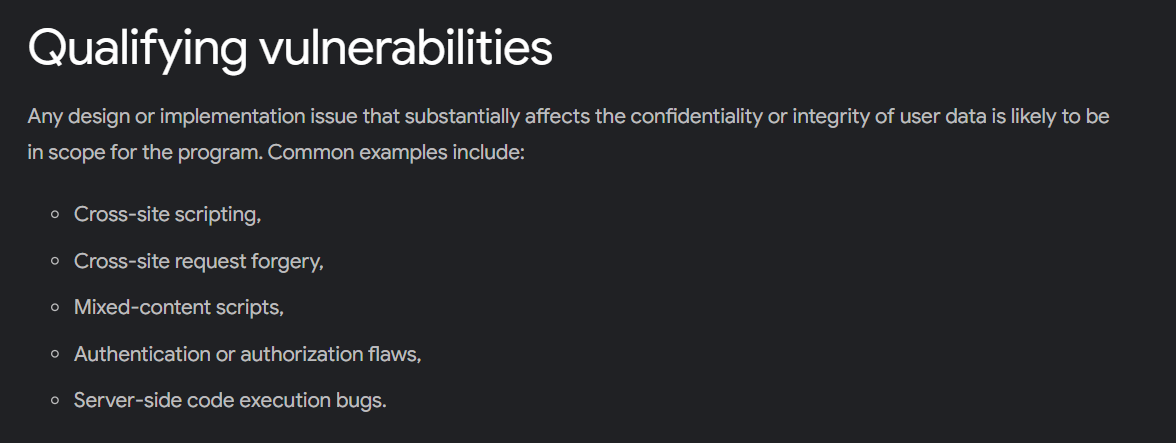
These bugs can roughly be categorized as high-severity security vulnerabilities, as they can lead to data breaches or significant data loss, compromise user devices and account details, etc.
After someone finds a bug, Google recommends using their Bug Hunter University resources as a guideline to send quality bug reports back to them.
They have a dedicated bug report page where individuals can report the bugs, which Google’s developers then analyze in defect triage meetings determining their priority and severity.
An interesting element that you can utilize is the way Google gamifies the program by showcasing individuals that report the most bugs on their leaderboard:
This program pays well, too. A total of 8.7 million dollars was paid to ethical hackers in 2021, with the first prize totaling a whopping 133,337 dollars.
Another example that showcases the importance of setting clear rules is PayPal’s program.
Their guidelines forbid hackers from using denial-of-service attacks, content spoofing, social engineering techniques, attacking PayPal’s physical locations, etc.
These terms are essential, as ethical hackers can try using every trick in the book to find a vulnerability and earn their reward—in PayPal’s case, the top prize is 20,000 US dollars for a critical-level issue.
Bug bounties are not here to introduce potential risks to users and your company but to find complicated defects that you can fix with the help of outside specialists.
For example, although a hacker can access a user’s account by impersonating a PayPal employee and getting their account details, this is not a vulnerability within PayPal’s services or codebase.
As you can see, by offering financial incentives and some recognition, while also providing clear rules and structure for participants to follow, you can organize a program mutually beneficial to your organization and outside experts.
Conclusion
Bug bounty programs and ethical hackers can be very effective at uncovering complex issues in your application, especially when combined with other bug testing practices.
This practice can save you a lot of trouble by preventing serious bugs from being exploited or damaging your users’ experience.
In this article, we tried to give you a general overview of bug bounty programs, their pros and cons, and how big tech companies implement them.
Through this explanation, we hope we have given you a solid understanding of this practice so you can decide if your company needs to start its very own bug bounty program.





