Bug bounty programs are an increasingly popular way to find and fix software vulnerabilities.
In this type of program, ethical hackers are invited to try to break into your system, but with one important premise—if they succeed, you’ll pay them for their work.
This approach can bring in many more submissions than traditional security testing alone and can help you find some of the most severe vulnerabilities in your app.
However, as you can imagine, launching a bug bounty program isn’t a walk in the park.
To help you get started, we’ve compiled an overview of the process and outlined some best practices.
Table of Contents
Ensure you have enough resources
Before launching a bug bounty program, it’s important that you have the resources and support in place to manage it effectively.
For starters, it’s a good idea to set a realistic budget and determine how much you are willing and able to spend on incentives.
To make the program more affordable to run, you may want to consider offering a range of reward tiers that correspond to the severity of the discovered vulnerabilities.
This can help to ensure that you’re offering the biggest rewards for the most valuable findings, while still providing incentives for hackers that find less severe bugs during the program.
In addition, it’s important to decide which team members or departments will be responsible for managing the program and allocate resources accordingly.

Get unreal data to fix real issues in your app & web.
For example, the marketing team needs to publicize the program, while the legal team will have to draft the contracts defining the relationship between the company and the ethical hackers who participate in it.
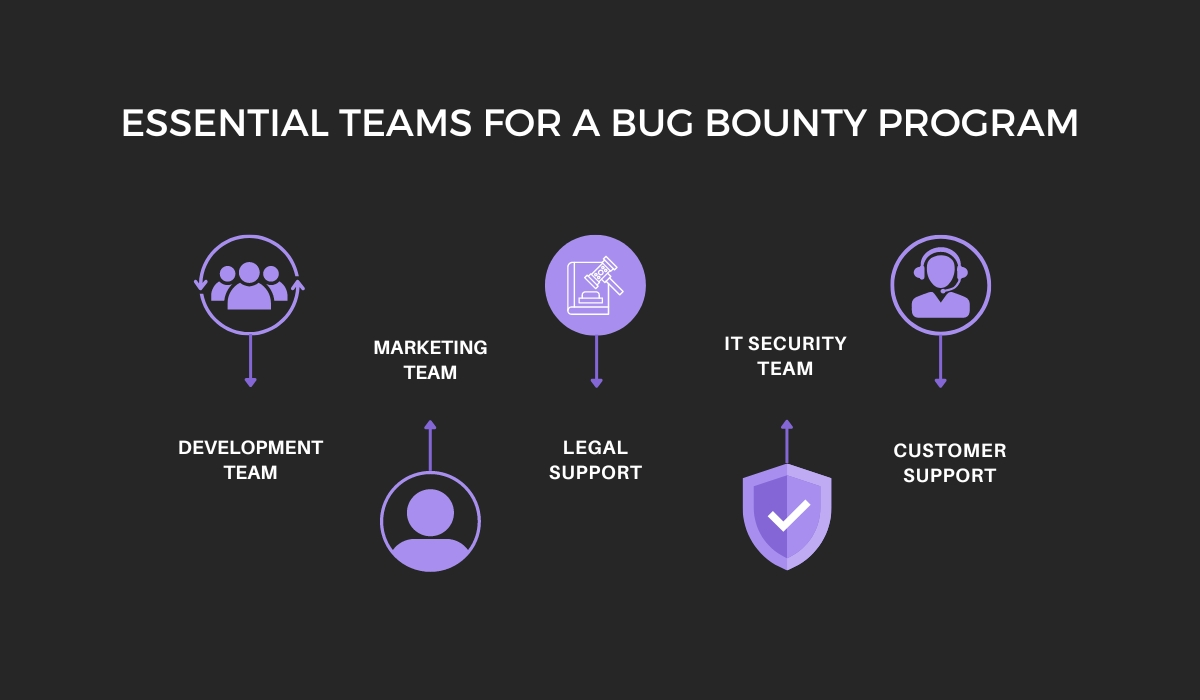
The program also needs developers who can incorporate new security patches, IT team members to ensure that the security is maintained, and customer support staff to handle the influx of inquiries from ethical hackers.
As you can see, there are many different aspects that go into building a bug bounty program.
It’s important to carefully consider all of these factors before implementing a program, as this will help ensure that you have the right processes in place to manage it effectively.
Determine the program’s scope
Scoping a bug bounty program provides ethical hackers with guidance on what to test, so it’s important to outline these rules at the outset.
Features within the scope should be tested, whereas those that have been declared out of scope should be excluded from the assessment.
Generally speaking, you should consider three main types of scope when developing your bug bounty program: limited, wide and open.
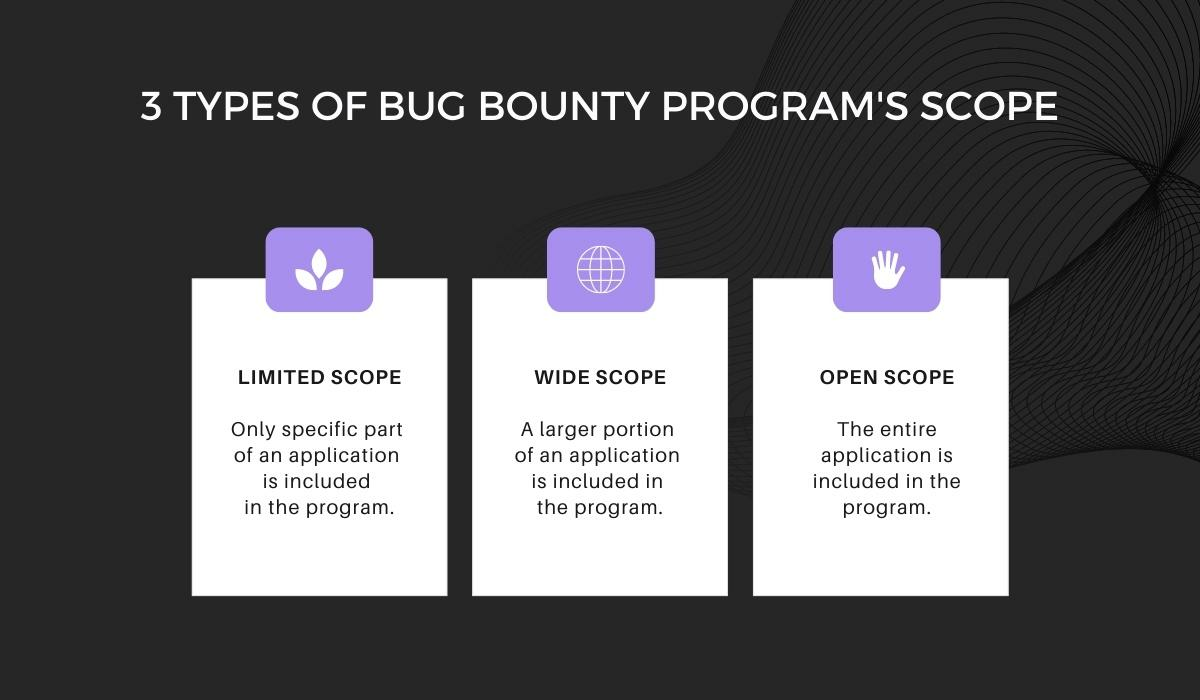
Limited scope restricts hackers to testing one specific area while leaving the rest of your application out of bounds.
It’s used when you need to prioritize your testing efforts and want to focus on a specific feature or functionality, usually one that is considered high-risk or critical.
On the other hand, in a wide-scope program, the scope is broader than in a limited-scope program but not as broad as it would be in an open-scope one.
In the example of BlaBlaCar, you can see that a wide-scope program can include mobile and web apps, APIs, and other different functionalities, meaning that hackers aren’t just testing one specific area but multiple ones.
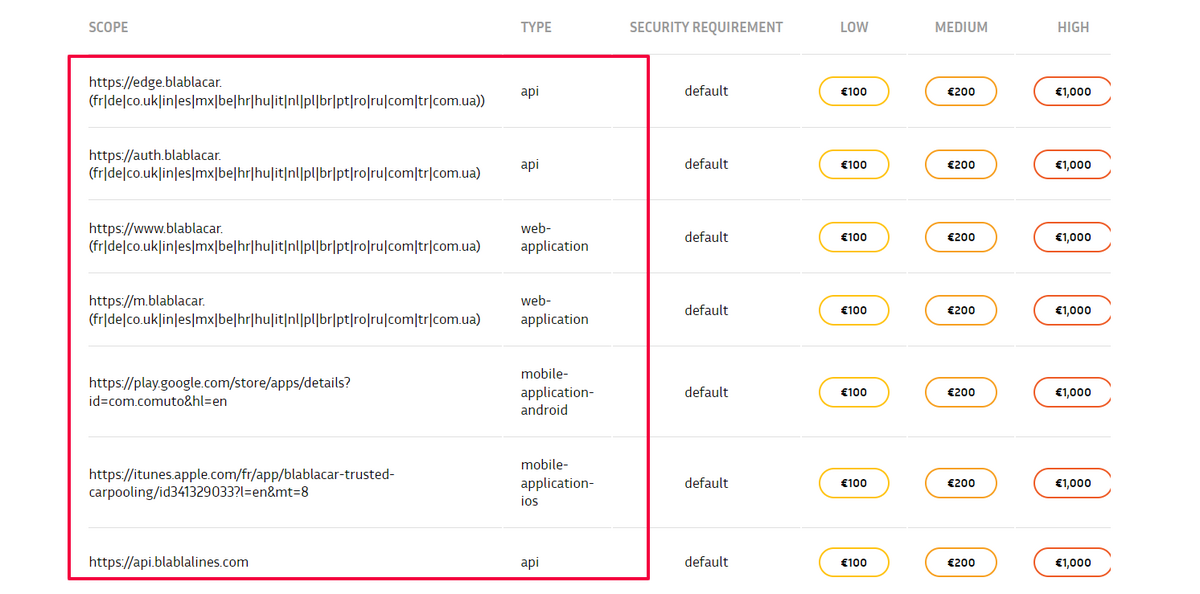
Over time, it would be wise to occasionally consider an open-scope bug bounty program that allows hackers to find anything they want.
This will help you spot any new trends in vulnerabilities, while giving you a better understanding of what malicious hackers are looking for when they’re trying to breach your security.
No matter which type of scope you choose, it’s essential to set clear rules and expectations for ethical hackers.
You want to make sure that everyone is aware of the main objective of the program, as well as what types of vulnerabilities you’re looking for and what type of data is off-limits.
Decide on the bug bounties
When considering how much ethical hackers should be paid for their efforts, it’s not so simple to come up with an appropriate figure.
There are a number of factors that you should consider here, including the type of bug being found, the severity of the bug, and how much time was spent finding it.
The more severe a bug is to your company’s security, the higher its payout should be.
For example, Zoom’s bug bounty program offers rewards ranging from $250 to $50.000 depending on the severity of the bug found—and in 2021, it paid out more than 1.8 million across 401 reports.
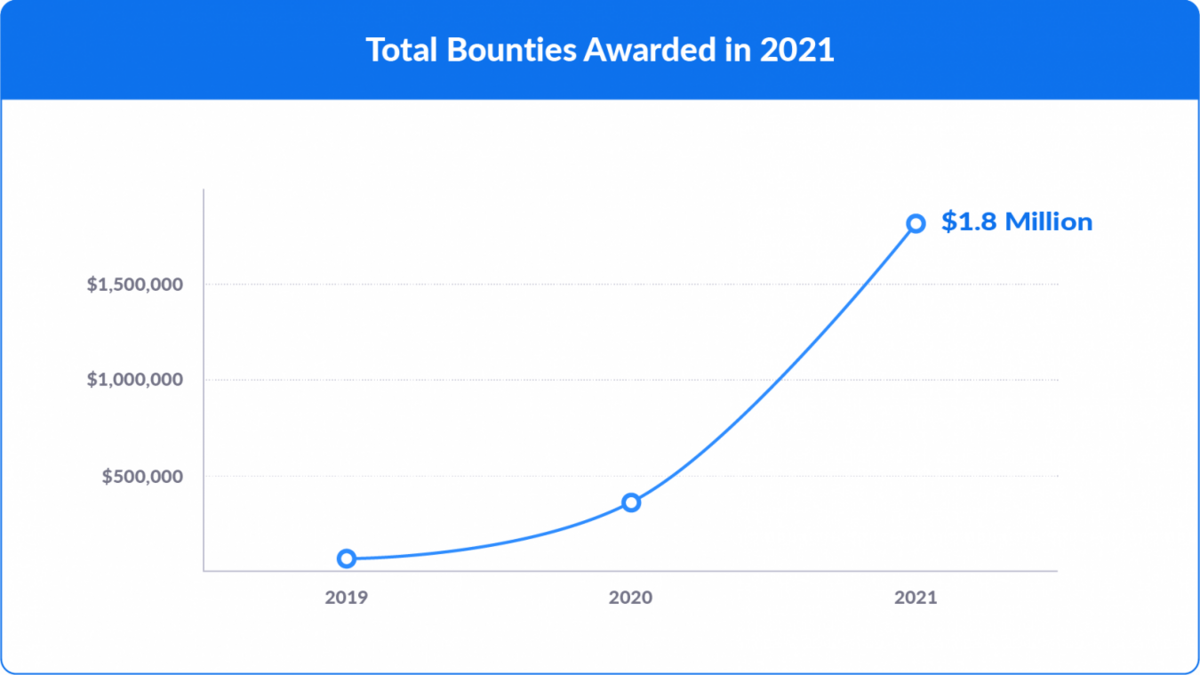
Although you may not be able to pay out as much as a company like Zoom does, it’s important to make sure that your bug bounty program is still appealing to hackers.
While giving them a T-shirt for their efforts may have been fine in the past, Leif Dreizler, a senior engineering manager at Twilio Segment, notes that giving hackers company swag is no longer an option.
At Twilio Segment, they pay different amounts for different types of vulnerability severity—including low, moderate, severe, and critical, as the picture below shows.
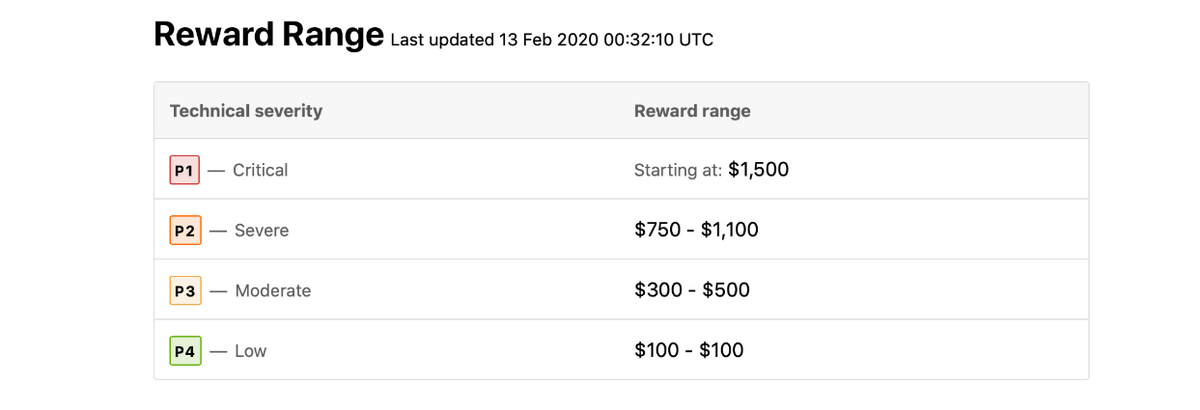
Most companies follow the same model, so this is essentially an industry standard.
However, what makes this company stand out from the crowd is that they emphasize that ethical hackers should be rewarded for any findings that bring value to the company, including duplicates and even well-written reports.
Ethical hacking is an investment in the company’s security.
The idea is that if you reward hackers for discovering vulnerabilities, even in situations where they didn’t find a real threat, they’ll be more likely to continue reporting flaws.
But if you don’t offer any sort of valuable compensation, they’ll move on to a company that does.
Set up a dedicated test environment
When running a bug bounty program, the most common choices for the testing environment are production and staging.
When deciding which one to use, you should consider the goals of the program, as well as the risks and benefits of using each environment.
For example, testing your app in a production environment is the most realistic way to find flaws.
Ethical hackers are testing for vulnerabilities using methods that mimic real-world hacking attempts, which will give you more accurate results than simulated data sets would.
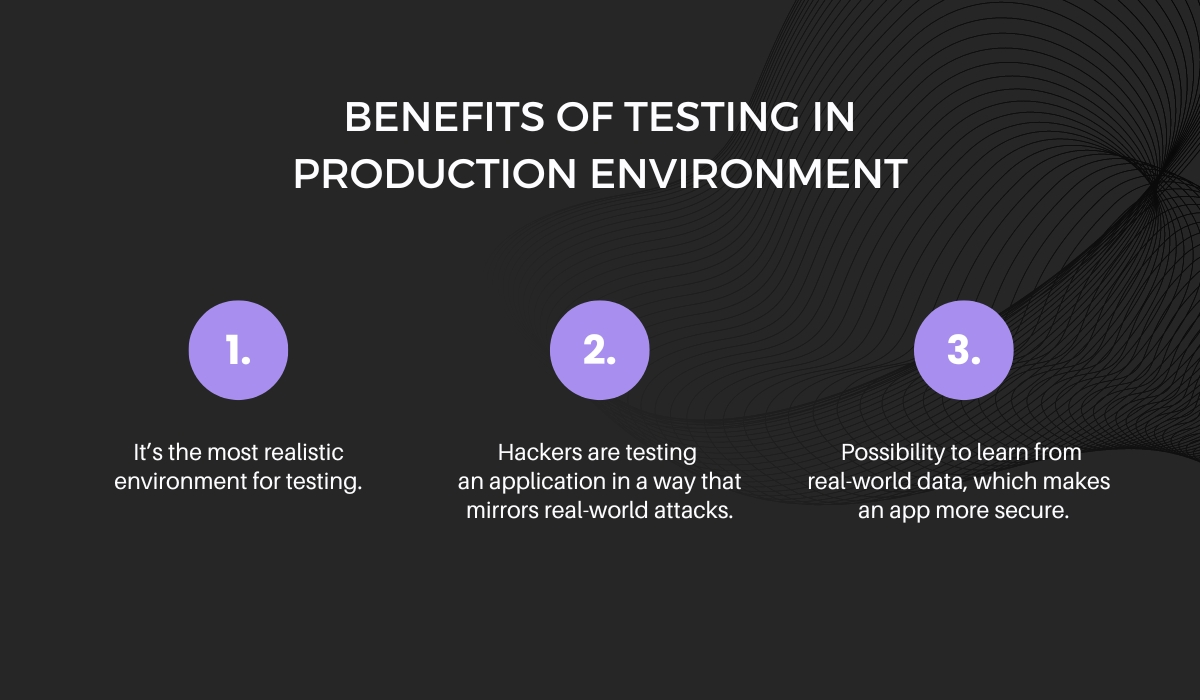
This, however, is not without drawbacks.
Using your production environment as a testing ground could have unintended consequences, such as slowing down app performance or causing users to experience issues.
You should also consider the risks involved with using real data and the potential for sensitive information to be exposed.
This can be avoided by using a staging environment instead.
A staging environment is a clone of your production app that has been configured for testing purposes.
You can use it to test for vulnerabilities when you don’t want to affect the original app and its users.
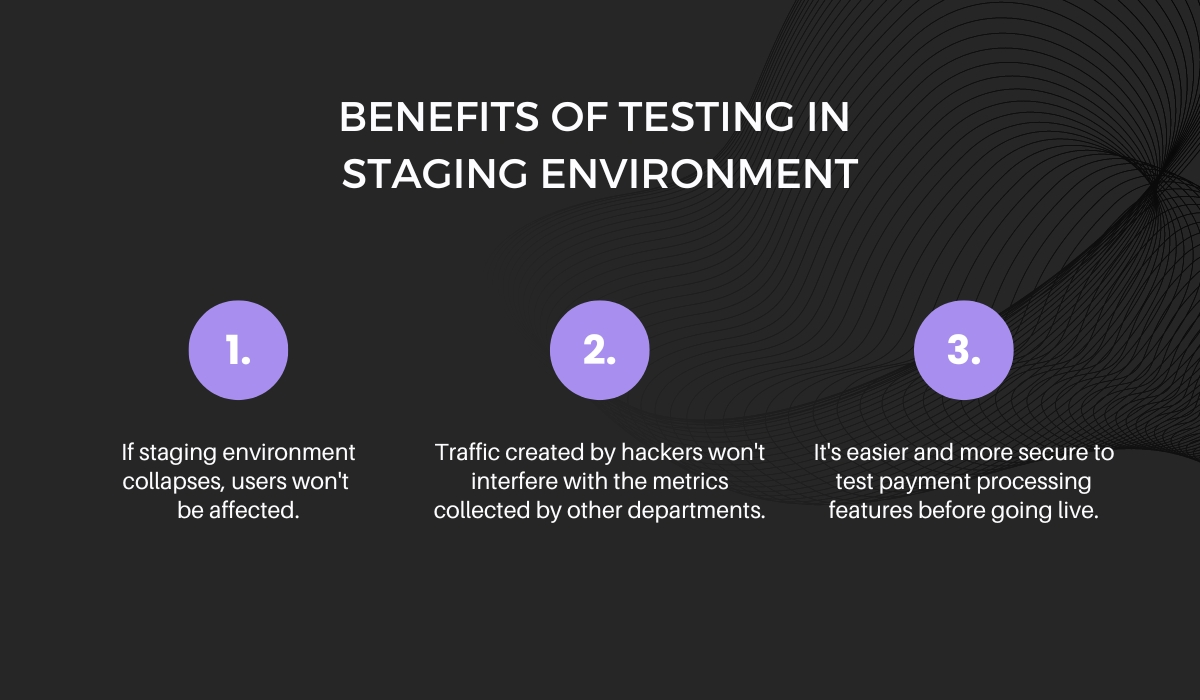
Additionally, if you want to test specific functions like payment processing, it may be easier to do so in this kind of environment because hackers can use fabricated credit cards, bank accounts, and social security numbers that don’t belong to real people—and not worry about ruining anything.
In general, using the production environment can provide more realistic and valuable results, but it may also carry higher risks.
Using the staging environment can provide a safer and more controlled environment for testing, but it may also produce less realistic results.
It would be best to combine both, but if you don’t have the time or resources to do so, you should at least use staging to make sure your app works as expected before putting it into production.
Create a vulnerability disclosure policy
A vulnerability disclosure policy is a must-have for any bug bounty program, but many don’t realize this until they experience the consequences of not having one in place.
Without a well-defined policy, you risk losing credibility, wasting time on low-value bugs, and possibly even facing legal action.
According to Intigriti’s research, there is also a chance that a significant percentage of vulnerabilities will go undetected.
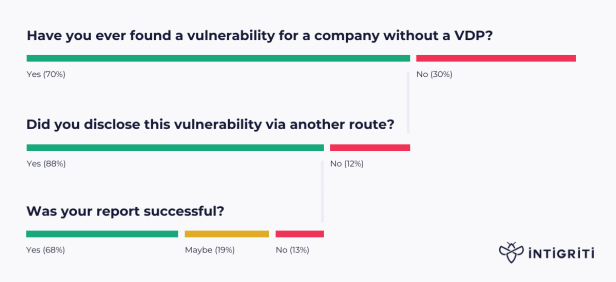
For these reasons, a vulnerability disclosure policy is one of the most critical elements of any successful bug bounty program.
A typical policy can be broken down into several sections:
- bug bounty program details, including the scope and payout
- instructions on how to report a vulnerability
- contact information in case of additional questions
- legal safe harbor
As you can see, ethical hackers consider this document of paramount importance, because it defines the scope and rewards for the bug bounty program.
It also gives them a clear legal framework within which to report bugs.
For example, if you look at Randstad’s vulnerability disclosure policy, you’ll see that they’ve included a legal safe harbor.
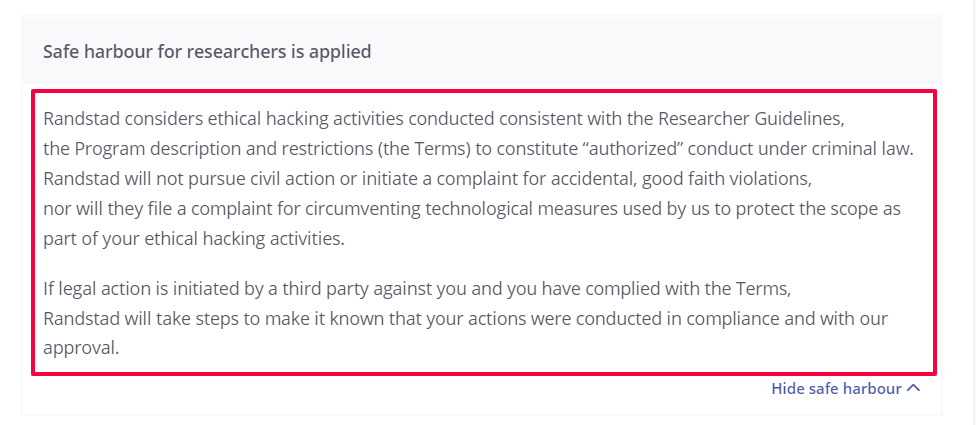
This is something that ethical hackers will be looking for, as it allows them to report vulnerabilities without worrying about legal ramifications, so you should also include it in your policy.
It’s important to take the time to write a solid vulnerability disclosure policy.
Only this way can you make sure that your program is both effective and legally sound.
Do a test run of the program
If you want to ensure the success of your bug bounty program, it’s a good idea to start off with a smaller test version and work out any kinks before rolling it out in its full form.
A test run will help you understand the challenges associated with managing a large number of ethical hackers and enable you to set up processes to handle a variety of situations, such as:
- how quickly you can verify and confirm vulnerabilities found by ethical hackers
- how many reports you can process in a given time period
- how well you can respond to issues discovered by ethical hackers
- how many participants in your program you can support
This will also allow you to test your systems and tools and make any necessary adjustments before starting the program.
By this point, you may find yourself having difficulty hiring ethical hackers.
This is not uncommon.
In fact, many companies today turn to third-party agencies that specialize in ethical hacking and bug bounty programs simply because they don’t have the time or resources to manage an in-house program.
If you’re in the same boat, you can consider working with companies such as Bugcrowd or HackerOne.
As both of these platforms specialize in running bug bounty programs and have a robust community of ethical hackers that you can tap into for your pilot test, they can help you get started more easily.
Once you finish your test run, you’ll have a better idea of how to conduct your full-fledged program.
You’ll also be able to make better decisions about how to structure it, what vulnerabilities to reward, and how to handle reports and issues found.
Promote the bug bounty program
If you’re running a public bug bounty program and are looking to attract more submissions, it might be helpful to promote it through different channels.
This will help get the word out about the program and encourage more people to participate.
For example, you could include a banner on your homepage with a link to the program or even create an entire website for it—as Google did.

Google launched Bug Hunters as a platform for ethical hackers to report vulnerabilities directly to Google.
There, it offers information about the program, the resources needed for bug hunting, and even a leaderboard with the names of the most successful contributors.
You can also advertise your program through social media by posting a callout on your company’s Twitter, Facebook or LinkedIn accounts, as in the picture below.
The great thing about this method is that it also encourages your followers—who don’t necessarily have to be ethical hackers—to report any bugs they find while using your app.
Another effective way to promote your program is to reach out to relevant communities—such as hacker conferences or meetup groups—to share information about the program.
This way, you can attract quality hackers who may have the potential to become your top performers.
You can choose to implement one of these strategies or try them all until you discover a combination that works best.
The important thing is to find a way to spread awareness about your program and encourage participation.
Conclusion
Launching a bug bounty program can be a highly effective tool for you to resolve vulnerabilities in your app.
By defining the scope, setting aside a budget for bounties, selecting a testing environment, and promoting your efforts to attract submissions from outside hackers, you can create a program that will significantly improve the quality of your app.
While implementing a bug bounty program requires some effort and resources, the benefits of increased security and enhanced reputation can make it well worth the investment.
Bug bounty programs are a popular way to find and fix bugs. We’ll give you an overview of the steps involved in launching a bug bounty program.





